Operational Controls and Classified Information Systems
Operational Controls and Classified Information Systems
By: Jeffrey W. Bennett, SFPC, SAPPC, ISOC, ISP

This article addresses the protection of Information Systems and the information that resides on them and is modeled after questions from the Self Inspection Handbook for NISP Contractors. We feel this is a great format to walk through the self-inspection criteria. We begin with the topic question, the NISPOM reference, an explanation of requirements, and finally how to inspect compliance.
Topic Question(s):
How is the IS physically protected? (Check all that apply)
NISPOM Reference(s):
8-302b Operational Controls
Discussion:
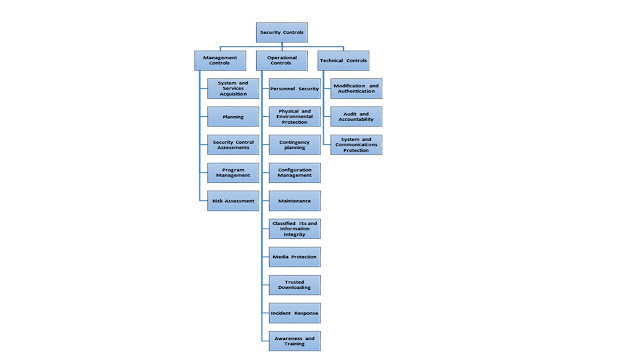
Each of the countermeasures above are already covered in sections of NISPOM chapter 5. Neither NISPOM nor the Self-Inspection Handbook desire to define these countermeasures. The intent is to determine which countermeasures are applied to demonstrate their application. These countermeasures should reflect the three controls identified in NISPOM for the protection of IS (Figure 1):
• Management
• Operational
• Technical
Figure 1 Security Controls
NISPOM 8-302, Operational Controls “…operational controls are methods primarily implemented and executed by people (as opposed to systems) to improve system security..”. The specific Operational Control in NISPOM 8-302b is Physical and Environmental Protection (Figure 2) which includes the following topics:
1. Limit physical access into ISs operating environments to authorized individuals
2. Protect the physical plant and support infrastructure for ISs
3. Provide supporting utilities for ISs, protect ISs against environmental hazards, and provide appropriate environmental controls in facilities containing ISs, when required by contract
Figure 2 Security Controls
Explanation:
Limiting physical access into ISs operating environment. Contractors are to limit access into the operational environment to that necessary to protect national security information as defined in Executive Order 13526. This E.O. identifies what national security information is and who has access to that information. As a review, the contractor establishes the security program designed to protect classified information. Where classified information contractually resides on information systems, the contractor is responsible for protecting the information at the appropriate classification level and releasing it to only those with the clearance and need to know. It is up to the contractor to protect the information and determine who has authorized access. Since the contractor has a contractual need to possess the classified information on an IS they are responsible for protecting the infrastructure that the classified information resides on. This includes the facility, the room in the facility, the classified IS and any classified storage equipment.
Protect the physical plant and support infrastructure for ISs. This requires preventing unauthorized persons from physically accessing the location where the classified IS resides. The computers, printers, etc should reside in a protected area that has limited access. Not only should there be measures to keep unauthorized persons from gaining authorized access, but there should be protection against breaking into the operational areas. Alarms, hardened equipment, approved locks and infrastructure should be part of the measures provided to and approved by the CSA.
Provide supporting utilities for ISs, protect ISs against environmental hazards, and provide appropriate environmental controls in facilities containing ISs, when required by contract. The ISs require environmental support such as air-conditioning, power, humidity control, to function correctly, overheating and lack of power will cause the IS to fail. This also may require hardening the area containing classified IS from natural disasters.
Additionally, the protective measures such as alarms and access controls require power to operate. NISPOM requires confidentiality or protection of classified information from unauthorized access and contractor security programs should protect classified information. However, protection concerning loss of availability or integrity of the information on the system are not a NISPOM requirement but may be directed by contract.
Validation:
1. Inspect Operational controls and determine how IS is protected (ie alarms, closed areas, alarms, guards.)
2. Determine how well controls in place are adequate for limiting access to information on IS.
3. Determine how well controls in place are adequate for limiting access to areas where classified IS resides.
4. When required by contract, determine how well controls in place are adequate for protecting IS against environmental hazards.
By: Jeffrey W. Bennett, SFPC, SAPPC, ISOC, ISP

This article addresses the protection of Information Systems and the information that resides on them and is modeled after questions from the Self Inspection Handbook for NISP Contractors. We feel this is a great format to walk through the self-inspection criteria. We begin with the topic question, the NISPOM reference, an explanation of requirements, and finally how to inspect compliance.
Topic Question(s):
How is the IS physically protected? (Check all that apply)
NISPOM Reference(s):
8-302b Operational Controls
Discussion:
Each of the countermeasures above are already covered in sections of NISPOM chapter 5. Neither NISPOM nor the Self-Inspection Handbook desire to define these countermeasures. The intent is to determine which countermeasures are applied to demonstrate their application. These countermeasures should reflect the three controls identified in NISPOM for the protection of IS (Figure 1):
• Management
• Operational
• Technical
Figure 1 Security Controls
NISPOM 8-302, Operational Controls “…operational controls are methods primarily implemented and executed by people (as opposed to systems) to improve system security..”. The specific Operational Control in NISPOM 8-302b is Physical and Environmental Protection (Figure 2) which includes the following topics:
1. Limit physical access into ISs operating environments to authorized individuals
2. Protect the physical plant and support infrastructure for ISs
3. Provide supporting utilities for ISs, protect ISs against environmental hazards, and provide appropriate environmental controls in facilities containing ISs, when required by contract
Figure 2 Security Controls
Explanation:
Limiting physical access into ISs operating environment. Contractors are to limit access into the operational environment to that necessary to protect national security information as defined in Executive Order 13526. This E.O. identifies what national security information is and who has access to that information. As a review, the contractor establishes the security program designed to protect classified information. Where classified information contractually resides on information systems, the contractor is responsible for protecting the information at the appropriate classification level and releasing it to only those with the clearance and need to know. It is up to the contractor to protect the information and determine who has authorized access. Since the contractor has a contractual need to possess the classified information on an IS they are responsible for protecting the infrastructure that the classified information resides on. This includes the facility, the room in the facility, the classified IS and any classified storage equipment.
Protect the physical plant and support infrastructure for ISs. This requires preventing unauthorized persons from physically accessing the location where the classified IS resides. The computers, printers, etc should reside in a protected area that has limited access. Not only should there be measures to keep unauthorized persons from gaining authorized access, but there should be protection against breaking into the operational areas. Alarms, hardened equipment, approved locks and infrastructure should be part of the measures provided to and approved by the CSA.
Provide supporting utilities for ISs, protect ISs against environmental hazards, and provide appropriate environmental controls in facilities containing ISs, when required by contract. The ISs require environmental support such as air-conditioning, power, humidity control, to function correctly, overheating and lack of power will cause the IS to fail. This also may require hardening the area containing classified IS from natural disasters.
Additionally, the protective measures such as alarms and access controls require power to operate. NISPOM requires confidentiality or protection of classified information from unauthorized access and contractor security programs should protect classified information. However, protection concerning loss of availability or integrity of the information on the system are not a NISPOM requirement but may be directed by contract.
Validation:
1. Inspect Operational controls and determine how IS is protected (ie alarms, closed areas, alarms, guards.)
2. Determine how well controls in place are adequate for limiting access to information on IS.
3. Determine how well controls in place are adequate for limiting access to areas where classified IS resides.
4. When required by contract, determine how well controls in place are adequate for protecting IS against environmental hazards.
Join our newsletter for more articles:



Comments